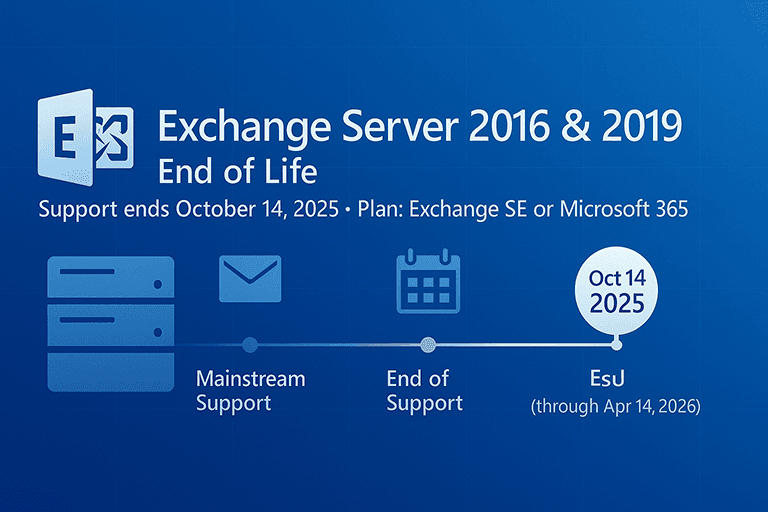
Why Computer & Server Costs Are Rising So Fast in 2026
If you’ve priced new desktops, laptops, or servers lately, you’ve probably noticed quotes are higher, “good” pricing expires faster, and lead times can be unpredictable. In 2026, a big driver isn’t just CPUs, it’s the parts that quietly make everything work: memory (DRAM) and storage (NAND/SSD). Driven by intense AI