Exchange Server 2016 & 2019 End of Life: Dates, Risks, and Your Upgrade Options
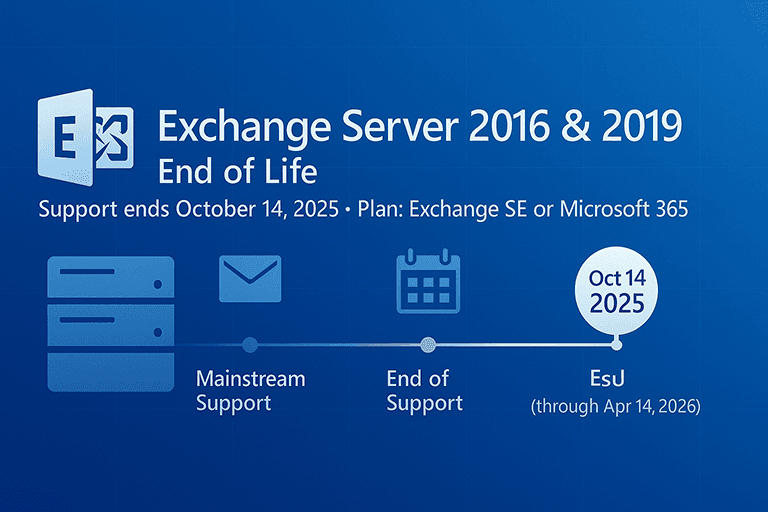
Exchange Server 2016 & 2019 End of Life: Dates, Risks, and Your Upgrade Options If your organization still runs Microsoft Exchange Server 2016 or 2019, a critical deadline is approaching. On October 14, 2025, both products reach end of support (often called “end of life” or EOL). That date affects your security posture, compliance, and IT budget planning, so now is the time to map your migration or upgrade path if you haven’t already started. What is Exchange Server? Microsoft Exchange Server is the on-premises backbone for business email, calendars, contacts, and collaboration. It powers Outlook (desktop, web, and mobile), integrates with security and compliance controls, and can run entirely on-prem or in a hybrid configuration with Microsoft 365 (Exchange Online). Most midsize and enterprise environments either run Exchange fully on-prem, fully in the cloud, or a hybrid approach to support a phased move. Exchange Server Life Cycle Explained The life cycle for Exchange server starts with mainstream support before moving into extended support, and finally reaching EOL. Here is a breakdown of the life cycle for Microsoft Exchange Server. Mainstream Support is the first phase and this typically includes the first five years after release. During this time you get the whole package: security updates, non-security fixes, the ability to request design changes/new features, plus both self-help and paid technical support. In short, this is when the product is actively improved and fully supported by Microsoft. Extended Support follows and runs (for most fixed-policy products) up to five additional years. You still receive security updates at no additional cost and can use paid support, but Microsoft no longer accepts requests for new features or most non-security fixes. You must also be on a supported service pack/CU level to stay covered. This phase keeps you secure, but it’s essentially in maintenance mode during this phase. Beyond End of Support (EOS) or once Extended Support ends, the product keeps working, but Microsoft stops providing new security updates, non-security updates, and assisted support. Self-help resources (docs/KBs) remain available, and Microsoft notes those are available for at least 12 months after EOS, but new fixes won’t arrive. Running past EOS therefore increases security and compliance risk over time. Extended Security Updates (ESU) is a special, last-resort program some legacy products can buy after EOS to receive Critical and/or Important security fixes only; it’s not full support and doesn’t add features or general hotfixes. Microsoft’s general ESU terms cover up to three years for certain products, but Exchange Server 2016 and 2019 have a unique, one-time ESU: six months of potential security updates (if any are needed) after October 14, 2025, and ending April 14, 2026. Microsoft is emphasizing this doesn’t extend the support lifecycle. Updates will be provided privately to ESU customers, and there’s no guarantee any updates will be released during that window. If you’re on Exchange 2016/2019 today, the practical takeaway is: plan to upgrade (e.g., to Exchange Server Subscription Edition) or move to Microsoft 365 before EOS. Treat ESU as emergency runway only. What Does Exchange Server End of Life Mean for Me? Microsoft Exchange Server 2016 and 2019 both exit support on October 14, 2025. After that, Microsoft will no longer provide security updates, non-security fixes, or technical support. Time-zone updates also stop, which can quietly break calendaring. In other words, the software keeps running, but you’re on your own for bugs, vulnerabilities, and compatibility issues. One-time ESU safety net (April 2026) Microsoft has announced a one-time, paid Extended Security Updates (ESU) program for organizations that can’t complete their transition by the deadline. ESUs provide critical and important security updates for six months. This will be through April 14, 2026. The ESU program must be purchased by contacting Microsoft (they won’t appear in Windows Update). This is not an extension of mainstream support, it’s meant to be a limited bridge to buy extra time to move off Exchange Server 2016 or 2019. Treat ESU as emergency runway, not a strategy. Your Paths Forward You have three practical options: move to Microsoft 365 (Exchange Online), upgrade your on-premises servers to Exchange Server Subscription Edition (SE), or run a hybrid environment while you transition. Option 1: Migrate to Microsoft 365 (Exchange Online) For most organizations, moving to Exchange Online will simplify operations and improve resilience: Lower operational overhead. Microsoft handles patching, HA/DR, and scaling. Continuous features & security. You get the latest anti-phishing and compliance capabilities. Flexible migration methods. Choose Cutover, Staged, or Hybrid migrations depending on size, complexity, and co-existence needs. Which migration is right for you? Cutover: Small environments (typically <150–200 mailboxes) that can switch over a weekend. Staged: Legacy sources like Exchange 2003/2007 moving in batches. Hybrid: Best for larger or compliance-heavy orgs; provides rich coexistence, free/busy, and staged moves. Option 2: Stay on-premises and upgrade to Exchange Server SE If regulatory, sovereignty, or architectural constraints keep you on-prem, Microsoft released Exchange Server Subscription Edition (SE) on July 1, 2025. After October 14, 2025, SE will be the only supported on-premises edition of Exchange. Upgrade paths to SE: In-place upgrade from Exchange 2019 CU14 or CU15 to SE. Legacy upgrade from Exchange 2016: introduce new SE (or 2019) servers, move mailboxes/connectors, then decommission old servers. In-place from 2016 is not supported. Before you choose this route, validate system requirements and supported coexistence scenarios between 2016/2019 and SE. Why pick SE? You retain full control over data and change windows. Microsoft continues delivering updates and security fixes for the on-prem product line (post-2019) on a subscription cadence. Option 3: Hybrid as a long-term architecture Hybrid isn’t just a migration tactic—it can be your steady-state when certain mailboxes must remain on-prem while others live in the cloud. You’ll run Exchange SE on-premises and Exchange Online in Microsoft 365, connected through HCW and Microsoft Entra (Azure AD) synchronization. Why you should act before EOL Waiting until the last minute invites risk and cost. Here’s why proactive planning pays: Security exposure. Exchange has historically been targeted by sophisticated threat actors. Once
Exchange Server 2016 & 2019 End of Life: Dates, Risks, and Your Upgrade Options Read More »